Editor's note: In this opinion piece, Xapo Bank’s Chief Information Security Officer, Andrew Mannoukas, shares his perspective on how combining Multi-Party Computation (MPC) with a secure governance process sets a new standard for secure and scalable bitcoin custody.
For years, Bitcoin users faced a difficult choice between convenience and security. Hot wallets offered speed but left private keys vulnerable, while cold storage promised security but involved complex, slow procedures for every transaction. Many believed traditional cold storage was the ultimate safeguard. At Xapo Bank, we built our reputation as the “Fort Knox of Bitcoin” on this principle, using physical bunkers to protect customer assets. Our record was flawless – not a single Bitcoin was ever lost to a security breach.

However, as technology evolved, we recognised a fundamental flaw in the old model. Even the most secure cold storage has an inherent single point of failure: at some point, a complete private key must be assembled to sign a transaction. This creates risks, from misplaced seed phrases to the persistent danger of insider threats. We asked ourselves: what if a private key never had to exist in a single place at any time?
This question led us to a more advanced security model, one that leverages Multi-Party Computation (MPC) not as a standalone tool, but as a core component of a sophisticated, policy-driven security architecture.
Understanding MPC: A new foundation for key security
Multi-Party Computation is a cryptographic breakthrough that works on a simple principle: your Bitcoin private key never exists as a complete entity. Through a process called Distributed Key Generation (DKG), multiple parties can jointly create a shared key pair without the complete private key ever being held by a single entity.
Think of it this way:
Traditional security is like a safe with one key; whoever has the key opens the safe.
Multisig is like a safe that requires multiple keys from different people to open, but each person still holds a complete key that could be stolen or lost. And they all have to be in the same location to open the safe.
MPC is like a bank vault whose lock is split across multiple locations. Each location knows only a part of the unlocking code and enters it privately. The full combination is never seen, never stored, and no location knows what the others entered. The vault opens only when all parts are entered at the same time; then the codes reset, leaving nothing behind.
In our system, the private key is split into multiple pieces called "shards". For a transaction to be authorised, a required threshold of these shards must each sign their part of the transaction. The complete key is never reconstructed during this process, eliminating the risk of it being compromised in a single event.
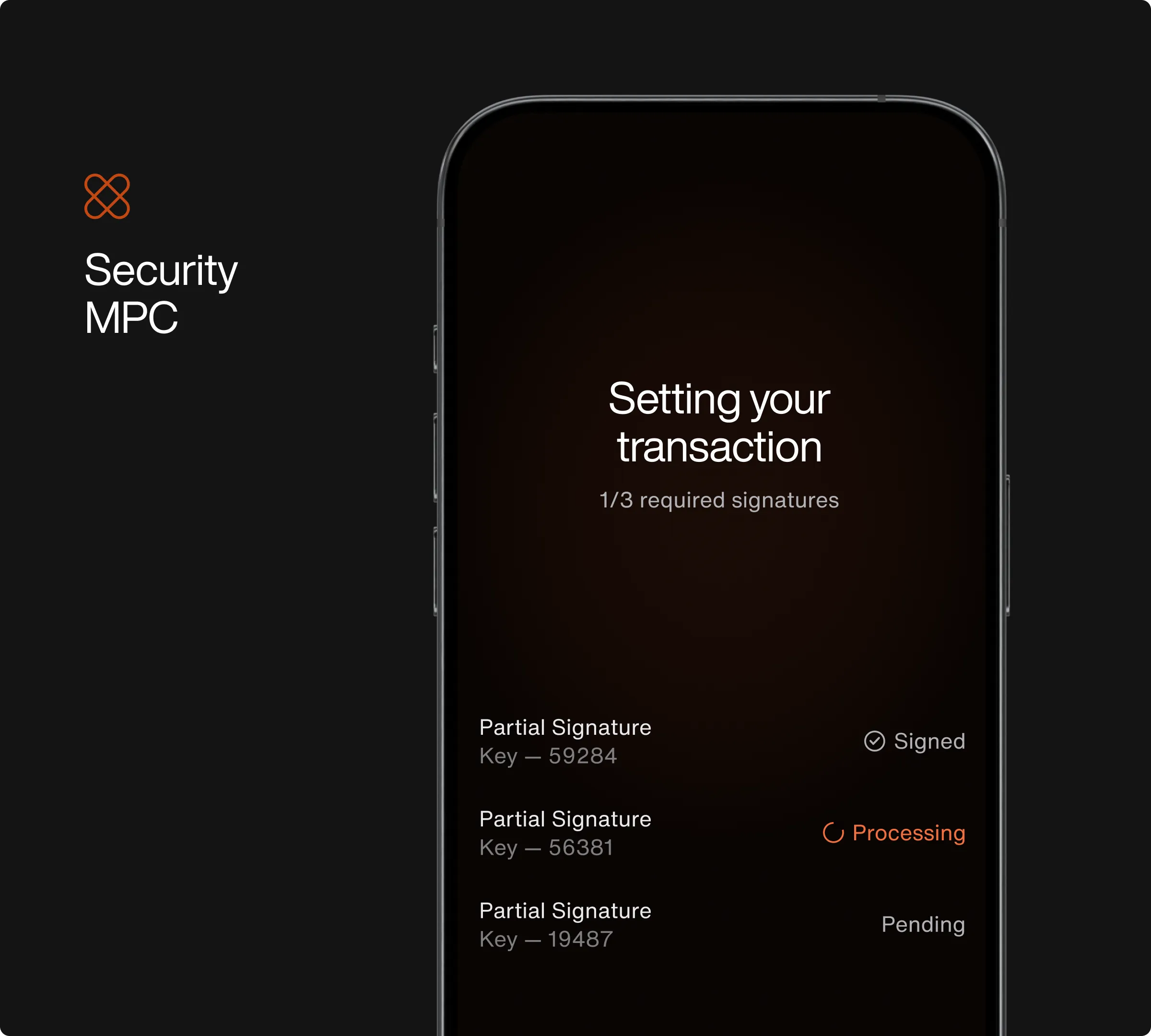
The limits of MPC alone
By itself, MPC is a massive leap forward, but it doesn't solve every security challenge, especially the risk of collusion or sophisticated internal threats. An MPC protocol on its own can't apply rules about who is authorised to initiate a transaction, for how much, or to what destination. This is where a second, crucial layer comes into play: governance.
The governance engine: The brains behind the operation
To achieve the highest level of security, we combined MPC technology with a powerful governance layer known as a "Transaction Authorisation Policy" (TAP) engine. If MPC provides the cryptographically secure "muscle," the TAP engine is the "brain" that enforces a strict set of rules.
This governance framework is what truly prevents unauthorised activity. It allows us to define and enforce highly specific rules, such as:
Transaction roles: It can dictate that a customer transaction must be initiated by the customer's device but co-signed by one of our secure Swiss bunkers.
Initiator controls: It can enforce a rule stating that treasury operations must be initiated by a member of the treasury team, not a customer service agent.
Quorum and thresholds: It defines precisely who needs to approve a transaction and in what combination. A high-value treasury operation might require approvals from the initiator, an internal stakeholder, and the Swiss bunker.
Amount limits: The engine can enforce limits on transaction values based on the type of operation or users involved.
Address whitelisting: The system can restrict outgoing transactions to a pre-approved list of addresses. Even if an attacker or rogue employee managed to get multiple approvals for a fraudulent transaction, the funds could not be sent to an unapproved address. Changing this list requires a significant quorum of approvals from a diverse set of internal stakeholders.
This governance layer effectively neutralises complex threats. Even if multiple individuals were compromised, the TAP engine and the bunker – which verifies raw transaction data – would reject an invalid request, preventing attacks like address poisoning where a scammer uses a similar-looking address.
Xapo's Layered Security: MPC and Governance in Action
Xapo Bank’s security model integrates the most advanced MPC protocols with this robust governance engine, creating a defence-in-depth system that is greater than the sum of its parts.
Our implementation includes:
Quantum-Resistant MPC: We use an advanced protocol known as MPC-CMP, which is widely regarded as resistant to threats from quantum computing.
Ephemeral key shards: The cryptographic shards used for signing are derived every minute, and all previous versions automatically become obsolete. An attacker would have to breach multiple, globally distributed physical locations and reverse-engineer the encryption in under 60 seconds.
Secure enclaves: Shards reside in offline, air-gapped secure enclaves. All computations happen within this encrypted environment, meaning the shard itself is never exposed to the operating system.
Decentralised and segregated governance: No single person or entity at Xapo has knowledge of where all the encrypted shards are located. This, combined with the TAP engine's rules, ensures that no single individual – not even myself as the CISO – can compromise the system.
The future of Bitcoin security is layered and regulated
Is traditional cold storage obsolete? In its conventional form, yes. A layered approach combining advanced MPC with a rigorous governance engine offers a far more resilient solution, addressing the single point of failure that has always plagued offline storage. We still maintain offline backups of the shards, but in a way that avoids creating a new single point of failure, ensuring we can recover assets under any circumstances.
For users, this institutional-grade architecture operates seamlessly in the background, providing the speed of a mobile wallet with a level of security that exceeds legacy systems. As a regulated financial institution, we are obligated to demonstrate this resilience to auditors and regulators. But most importantly, we must prove it to our customers, who deserve to know their savings are protected by the most advanced, multi-layered security framework available today.